Solution Overview
To provide a Hotspot WiFi solution that provide internet access through Cisco Identity Services Engine (ISE) by:
- Ensuring all guests are bandwidth limited to 5 Mbps during Internet access.
- Guests are able to connect during office hours only to the Hotspot SSID.
- Guests are provided access after accepting terms and conditions from the Hotspot portal provided.
- The Hotspot portal is provided through HTTPS.
- Redirection is enabled on WLCs to direct guests to the Hotspot portal automatically.
- Portal certificates are installed to secure the portal and enable user devices to trust the patient portal.
In this solution, the guest connect to the network with a wireless connection. Cisco ISE, using the Hotspot Guest portal, allow patient devices to connect to a private network by accepting terms and conditions.
The following is an outline of the subsequent Cisco ISE process:
- The network access device (NAD) sends a redirect to the Hotspot Guest portal.
- If the MAC address of the guest device is not in any endpoint identity group or is not marked with an Acceptable Use Policy (AUP) accepted attribute set to true, Cisco ISE responds with a URL redirection specified in an authorisation profile.
- The URL redirection presents the patient with an AUP page when the guest attempts to access any URL.
- If the guest accepts the AUP, the endpoint associated with their device MAC address is assigned to the configured endpoint identity group. This endpoint is now marked with an AUP accepted attribute set to true, to track the guest acceptance of the AUP.
- If the patient does not accept the AUP or if an error occurs, for instance, while creating or updating the endpoint, an error message displays.
- After the endpoint is created or updated, a Change of Authorization (CoA) termination is sent to the NAD.
- After the CoA, the NAD re-authenticates the patient connection with a new MAC Auth Bypass (MAB) request. The new authentication finds the endpoint with its associated endpoint identity group, and returns the configured access to the NAD.
Based on the Hotspot Guest portal configuration, the guest is directed to the business unit URL from where they are connecting.

Wireless LAN Controller
WLAN Configuration
Create a new SSID on the WLC by providing the following configuration under WLANs > WLANs:
| Setting |
Configuration |
| Profile |
Hotspot_Profile |
| SSID |
Hotspot |
| Interface |
Hotspot_interface |
| Layer 2 Security |
None |
| Mac Filtering |
Enabled |
| Layer 3 Security |
None |
| Captive Network Assistant Bypass |
Disable |
| AAA Servers – Authentication Servers |
Enabled
IP:x.x.x.x (Cisco ISE PSN), Port:1812 |
| AAA Servers – Accounting Servers |
Enabled
IP:x.x.x.x (Cisco ISE PSN), Port:1813 |
| QOS |
Silver (best effort) |
| QOS Application Visibility |
Enabled |
| Average Data Rate |
Downstream:5000 Upstream:5000 |
| Burst Data Rate |
Downstream:5000 Upstream:5000 |
| Average Real-Time Rate |
Downstream:5000 Upstream:5000 |
| Burst Real-Time Rate |
Downstream:5000 Upstream:5000 |
| Allow AAA Override |
Enabled |
| DHCP Addr. Assignment |
Enabled |
| NAC State |
ISE NAC |
Interface Configuration
The following VLAN interface parameters must be configured on the WLC to provide guest devices an ip-address under CONTROLLER > Interfaces:
| Setting |
| Interface Name |
| VLAN Identifier |
| Netmask |
| Gateway |
| IP Address |
| DHCP Server |
AAA Configuration
The Cisco ISE Policy Service Nodes (PSN) must be added to the WLCs as radius servers to provide AAA functions. Below is a screenshot example:

The ‘Auth Called Station ID Type’ were updated to indicate ‘AP Name:SSID’. This enables policies within Cisco ISE to look up the AP name onto which a patient connected to determine which hotspot portal are provided to that guest.

Access Control Lists
Two access control lists (ACL) were created in this case and are used within policy profiles when deploying the new Hotspot WiFi solution. These are:
- Guest_wifi_redirect – This ACL will only allow DNS services and access to the PSN nodes and deny all other traffic. This ACL will enable guest to be redirected to the Hotspot WiFi portal to accept terms and conditions after connecting to the SSID.
- Guest_permit – This ACL permits all traffic a guest is allowed or denied after accepting terms and conditions.
Cisco Identity Services Engine
Ensure the Cisco WLC is added as a NAD (Network Access Device) before completing the rest of the configuration.
Identity Group
Identity Groups are a collection of individual endpoints that share a common set of privileges that allow them to access a specific set of Cisco ISE services and functionality.
In this case, guest endpoints (MAC addresses) are placed in an Identity Group after the guests accepts the terms and conditions on the portal. These endpoints are purged after one day. This allows the creation of a policy that will allow guest endpoints in this group access to the network.
This group can be created under Administration > Identity Management > Groups > Endpoint Identity Groups. For this example we will call it HotspotEndpoints.
The purge policy to remove all endpoints daily from the HotspotEndpoints identity group can be created under Administration > Identity Management > Settings > Endpoint Purge.
Wildcard Certificate
In this example a wildcard certificate was used to secure the portal. A wildcard certificate uses a wildcard notation (an asterisk and period before the domain name) and allows the certificate to be shared across multiple hosts in an organisation. The wildcard notation of *.customerdomain.com (for example) must be imported to the Cisco ISE nodes as well as the root and intermediate certificates for the wildcard certificate within the trusted certificate store.
These certificates can be purchased from a public Certificate Authority (CA). Best practise would be to generate a certificate signing request (CSR) and upload it to the CA when purchasing the certificate.
This link will be helpful.
Time and Date Conditions
Time and date conditions let you set or limit permission to access Cisco ISE system resources to specific times and days as desired by the attribute settings you make.
Below is the ‘Time and Date Condition’ applied to my authorisation policies.

Portal Configuration
Cisco ISE has a default Hotspot Guest Portal that can be duplicated and customised to fit your company requirements. The diagram below indicates how to duplicate a portal.

Within the ‘Hotspot Guest Portal’ the following is a requirement:
- Under Portal Settings > Certificate group tag select the group your wildcard certificate belongs to. Most likely ‘Default Portal Certificate Group’.
- Under Portal Settings > Endpoint Identity Group select the identity group configured earlier.
- To include an acceptable use policy (AUP) go to ‘Acceptable Use Policy (AUP) Page Settings’ and select ‘Include an AUP page’.
- Within the ‘Authentication Success Settings’ configure the URL specific to the business units home webpage.
The diagram below shows where logos, banners, terms and conditions specific to the business unit and a colour scheme can be updated.

Below is an example of a hotspot portal.

Authorisation Profiles
Authorisation policies associate rules with specific user and group identities to create the corresponding profiles. Whenever these rules match the configured attributes, the corresponding authorisation profile that grants permission is returned by the policy and network access is authorised accordingly.
Two authorisation profiles was created for this example. The first authorisation profile will ensure when a guest endpoint connect to the SSID they are redirected to the correct portal and the ‘Guest WiFi redirect’ ACL are pushed down to the endpoint.
There will also be an authorisation profile that will grant guest endpoints access to the internet and push down ACL ‘Guest Permit’ to the endpoints.
To create these authorisation profiles go to Policy > Policy Elements > Results > Authorization > Authorization Profiles.
|
Authorisation Profile
|
ACL |
Redirect Portal |
Authorisation Policy |
Portal FQDN |
| Guest_WiFi_Redirect |
Guest_wifi_redirect |
Hotspot Portal |
Guest_WiFi_Redirect |
hotspot.customerdomain.com (Make sure there is a DNS entry) |
| Guest_WiFi_Permit |
Guest_permit |
NA |
Guest_WiFi_Permit |
NA |
Policy Sets
Policy sets enable you to logically group authentication and authorisation policies within the same set.
For this example a policy set was created specifically for the Hotspot WiFi solution. All authentication and authorisation policies for this solution are contained within this policy set. For endpoints to be allowed access within this policy set patients need to connect to the Hotspot SSID which has been configured as WLAN ID 4 on the WLC.
Create the policy set under Policy > Policy Sets and in my case the condition is Airespace:Airespace-Wlan-Id EQUALS 4.
Authentication policies define the protocols that Cisco ISE uses to communicate with the network devices, and the identity sources that is used for authentication. The authentication policy within the patient policy set allow all devices connecting through a wireless connection (as long as it connected to WLAN ID 4). Below is the configuration for my example.
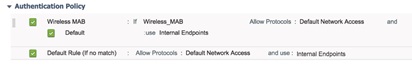
Authorisation policies can contain conditional requirements that combine one or more identity groups using a compound condition that includes authorisation checks that can return one or more authorisation profile. This example has two authorisation policies as per the table below:
| Authorisation Policy |
Condition |
Authorisation Profile |
| Guest_WiFi_Redirect |
Wireless_MAB
Guest endpoint must connect to an AP which name contains XXXXX (Make sure all APs in your deployment has those characters in it).
Guest can only connect week days during office hours. |
Guest_WiFi_Redirect |
| Guest_WiFi_Permit |
Wireless_MAB
Guest endpoint device must be in the ‘HotspotEndpoints’ identity group.
Patient can only connect week days during office hours. |
Guest_WiFi_Permit |













